If you didn’t catch the Washington Post “In the Loop” article by Al Kamen this week entitled “Counter terror calendar 2014 is out!,” you’ll be pleased to know that yes, the 2014 edition of the National Counterterrorism Center’s annual Counterterrorism Desk Calendar is now available for ordering on the U.S. Government Bookstore.
If you didn’t catch the Washington Post “In the Loop” article by Al Kamen this week entitled “Counter terror calendar 2014 is out!,” you’ll be pleased to know that yes, the 2014 edition of the National Counterterrorism Center’s annual Counterterrorism Desk Calendar is now available for ordering on the U.S. Government Bookstore.
Image: Cover of the 164-page 2014 Counterterrorism Calendar from the National Counterterrorism Center depicts the 2013 bombings at the Boston Marathon. Photo Credit: David L. Ryan / Boston Globe.
The goal behind the Counterterrorism Calendar is to educate and inform both professionals– first responders, military, intelligence, law enforcement and other counterterrorism personnel– as well as civilians about the threats of international terrorism and how to prevent, respond or mitigate these threats against the United States both at home and abroad.
History of U.S. Government Inviting Citizen Involvement in Domestic Security
Since its founding, America has had a history of inviting its citizens to participate in its own defense. Even with the danger of British sympathizers turning them in, brave revolutionaries posted recruiting posters on behalf of the Continental Congress such as the one below that invited Americans to “Take Notice” and help General Washington and the Continental Army defend against “the hostile designs of foreign enemies.”
 Image: This Revolutionary War recruiting poster urged brave and able-bodied young men to “take notice” and join forces with General Washington and the Continental Army in the fight against “foreign enemies,” in this case, the British. Photo Credit: Bettmann/CORBIS
Image: This Revolutionary War recruiting poster urged brave and able-bodied young men to “take notice” and join forces with General Washington and the Continental Army in the fight against “foreign enemies,” in this case, the British. Photo Credit: Bettmann/CORBIS
In World War 2, the Federal Government issued numerous similar domestic campaigns reminding citizens that it was their civic duty to “defend America” and inviting citizens to help support the war industry and to be vigilant against spies, saboteurs and other actions by the enemy both at home and abroad.
 Image: U.S. Government World War II propaganda poster urging civilians to participate in the war effort. Source: University of North Texas Digital Library
Image: U.S. Government World War II propaganda poster urging civilians to participate in the war effort. Source: University of North Texas Digital Library
Today, the war is a War on Terror, and the U.S. Government still needs involvement and vigilance of its citizens and allies, whether in the United States or abroad, to identify and protect against terrorists.
The 2014 Counterterrorism Calendar
Under the Office of the Director of National Intelligence, the National Counterterrorism Center or NCTC serves as the primary organization in the U.S. government for integrating and analyzing all intelligence possessed or acquired by the U.S. government about international terrorism, including data from U.S. Federal agencies like the CIA, NSA, Defense Intelligence Agency, and the FBI as well as other domestic and international sources.
First published in a spiral-bound daily planner format in 2003, just two years after the World Trade Center attacks, the Counterterrorism or CT Calendar from the NCTC is published annually. According to the NCTC, their 2014 Counterterrorism Calendar:
…provides information on known terrorist groups, individual terrorists, and technical information on topics such as biological and chemical threats.This edition, like others since the Calendar was first published in daily planner format in 2003, contains many features across the full range of issues pertaining to international terrorism: terrorist groups, wanted terrorists, and technical pages on various threat-related topics.
Features of the Calendar
In addition to serving as a desk calendar / event planner, the 164-page 2014 Counterterrorism Calendar also serves as a tutorial on international terrorism and a gallery of “most wanted” terrorists.
The right-hand page of the planner has the event planner dates along with key historical events of significance to terrorists that might be used to plan future terrorist activities. For example, on January 8, 1998, terrorist Ramzi Ahmed Yousef was sentenced to life plus 240 years for his role in the 1993 World Trade Center bombings.
On the left-hand pages are photos, maps and/or data on terrorists and terrorist organizations around the world, from Africa and the Middle East to Europe and the Americas.
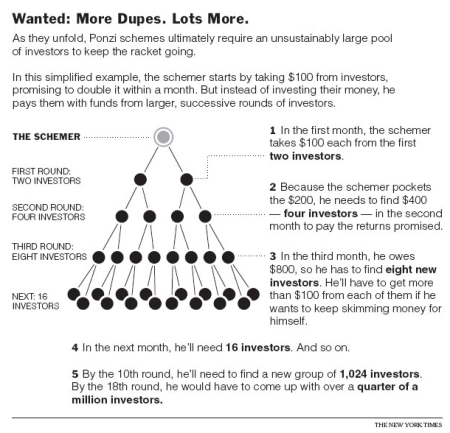
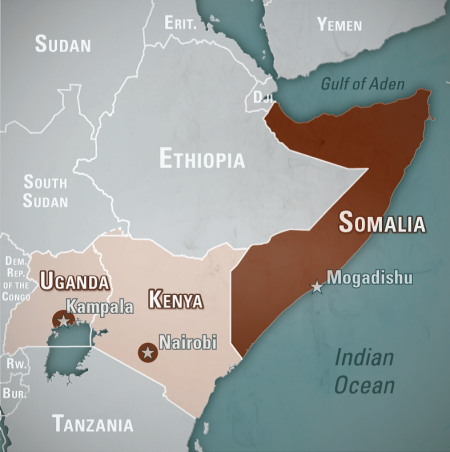 Image: Map denoting locations of major terrorist incidents likely committed by the Harakat Shabaab al-Mujahidin—commonly known as al-Shabaab, a “clan-based insurgent and terrorist group” operating in and around Somalia. Source: NCTC 2014 Counterterrorism Calendar
Image: Map denoting locations of major terrorist incidents likely committed by the Harakat Shabaab al-Mujahidin—commonly known as al-Shabaab, a “clan-based insurgent and terrorist group” operating in and around Somalia. Source: NCTC 2014 Counterterrorism Calendar
“Terrorism tutorial” information ranges from cultural—details about the Islamic Calendar; the spelling of Arabic names and terms; lists of Foreign Terrorist Organizations (FTOs), and logos used— to technical – information about Chemical-Biological-Radiological-Nuclear-Explosive (CBRNE) weapons commonly used by terrorists, from suicide bombs to sarin gas, and how to detect and mitigate them. For example, who among us would recognize the terrorist threat from these innocent-looking beans?
 Image: Photo of castor beans from which the deadly toxin ricin is extracted. Ricin is poisonous if inhaled, injected, or ingested. Source: NCTC 2014 Counterterrorism Calendar
Image: Photo of castor beans from which the deadly toxin ricin is extracted. Ricin is poisonous if inhaled, injected, or ingested. Source: NCTC 2014 Counterterrorism Calendar
“Wanted” Terrorists
Providing the real drama of the calendar are the full-page “Wanted” poster-style pages of an individual terrorist, complete with photo (if available), aliases, his terrorist activities, the reward offered, and how to report information about him.
One of the largest rewards, $25 Million, is offered for information leading to the capture of Ayman al-Zawahiri, also known as “The Teacher” or “The Doctor” who is a physician and the founder of the Egyptian Islamic Jihad. According to the CT Calendar:
“This organization opposes the secular Egyptian Government and seeks its overthrow through violent means. Al-Zawahiri is believed to have served as an advisor and doctor to Usama Bin Ladin. He has been indicted for his alleged role in the August 7, 1998, bombings of the US embassies in Dar es Salaam, Tanzania, and Nairobi, Kenya. The embassy bombings killed 224 civilians and wounded over 5,000 others.”
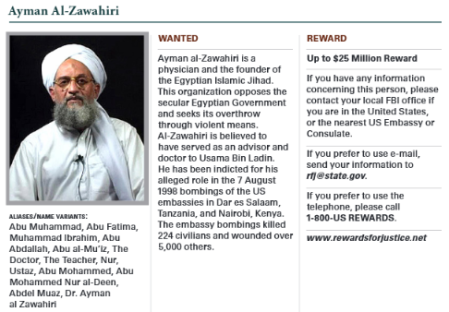 Image: Extract from the “wanted” page of Ayman al-Zawahiri, Al-Qaida leader and founder of Egyptian Islamic Jihad. Source: NCTC 2014 Counterterrorism Calendar
Image: Extract from the “wanted” page of Ayman al-Zawahiri, Al-Qaida leader and founder of Egyptian Islamic Jihad. Source: NCTC 2014 Counterterrorism Calendar
Civilian Involvement
Finally, the NCTC carries on the civilian involvement tradition by including instructions for citizens of the U.S. and other countries on how they can help fight terrorism. Pages on” Indicators of False Travel Documents”, “Radicalization”, and how U.S. residents can report suspicions are provided. Additionally, the Rewards for Justice (RFJ) Program is described in detail, wherein the U.S. Secretary of State may offer rewards for information that prevents or favorably resolves acts of international terrorism against US persons or property worldwide.
On the last page is a Bomb Threat Call Procedures form with valuable details of questions to ask and information to note about the caller, such as his or her voice (accent, age, tone, language) and background sounds. Did you note if the caller was clearing his throat or had an accent? Were there sounds of machinery in the background? What kind? Any and all details could help law enforcement.
 Image: Table from the Bomb Threat Call Procedures form. Source: Page 160 of the 2014 Counterterrorism Calendar.
Image: Table from the Bomb Threat Call Procedures form. Source: Page 160 of the 2014 Counterterrorism Calendar.
Forewarned is Forearmed
Like the tradition of the best Government civilian campaigns since the founding of the Nation, the National Counterterrorism Center’s annual Counterterrorism Calendar is simultaneously meant to alert and inform us, making both civilians and professionals alike aware of the very real dangers around us and educating us on what—and whom—to look for. With the cover photo depicting the 2013 bombings at the Boston Marathon– where ordinary citizens were instrumental in identifying and locating the terrorists responsible– the importance of having an informed and involved citizenry has never been clearer.
How can I get a copy of the National Counterterrorism Center’s 2014 Counterterrorism Calendar?
- Shop Online: You can purchase this calendar from the U.S. Government Online Bookstore at http://bookstore.gpo.gov by:
- Order by Phone: Call our Customer Contact Center Monday through Friday, 8 am to 5:30 pm Eastern (except US Federal holidays). From US and Canada, call toll-free 1.866.512.1800. DC or International customers call +1.202.512.1800.
- Shop our Retail Store: Buy a copy of any print editions from this collection at GPO’s retail bookstore at 710 North Capitol Street NW, Washington, DC 20401, open Monday–Friday, 9 a.m. to 4 p.m., except Federal holidays, Call (202) 512-0132 for information or to arrange in-store pick-up.
- Visit a Federal Depository Library: Search for it in a nearby Federal depository library or download a PDF version.
About the Author: Government Book Talk Editor Michele Bartram is Promotions Manager for GPO’s Publication and Information Sales Division in Washington, DC, and is responsible for online and offline marketing of the US Government Online Bookstore (http://bookstore.gpo.gov) and promoting Federal government content to the public.
 The United States Sentencing Commission Guidelines Manual is a comprehensive document that provides federal judges with recommendations on appropriate sentences for individuals convicted of federal crimes. It’s a tool designed to promote consistency and fairness in sentencing across the country. The new U.S. Sentencing Commission Guidelines Manual 2025 is now available for order from the U.S. Government Bookstore.
The United States Sentencing Commission Guidelines Manual is a comprehensive document that provides federal judges with recommendations on appropriate sentences for individuals convicted of federal crimes. It’s a tool designed to promote consistency and fairness in sentencing across the country. The new U.S. Sentencing Commission Guidelines Manual 2025 is now available for order from the U.S. Government Bookstore.


 Posted by Trudy Hawkins
Posted by Trudy Hawkins